Search This Blog
DesertLiving—IT
Fundamentals of Information Technology
Posts
Doing What’s Right to Protect Your Network
Latest Posts
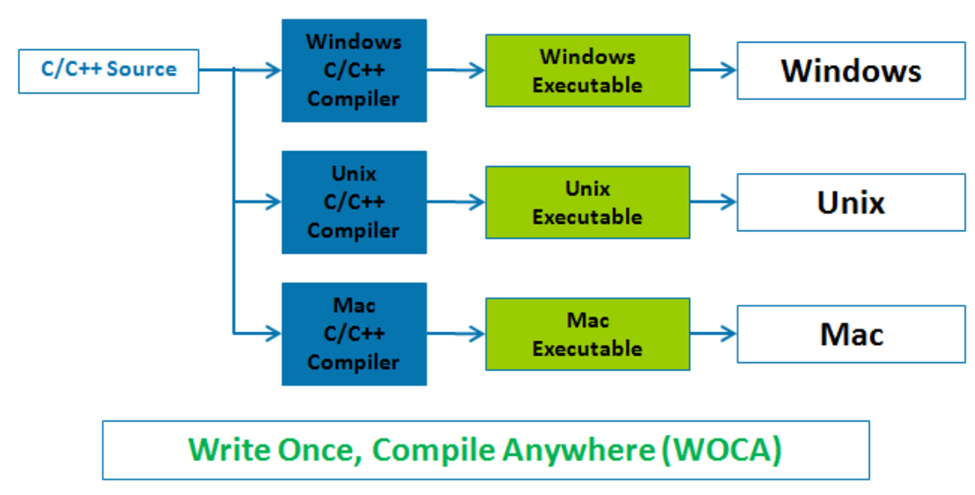
Object-Oriented-Programming helps programmers develop programs, which can store knowledge, state, data, and do work/tasks. Java programmers use a class as a standard of what an object can do. A method modifies a class state (applicable to all class instances), and an instance represents a class. Java has a simple and clean coding style that does not require complex features. The ability to integrate compiled languages and interpreted languages with Java compiler (javac) and Java Virtual Machine (JVM) makes Java popular choice. Java uses a platform-independent to execute a compiled program on any machine by converting source code into intermediate code that can run on any hardware JVM compliant. Java’s write-once-run-anywhere means that it can run on any operating system.
The concept behind Java is its four pillars of Object-Oriented Programming: encapsulation, data abstraction, polymorphism, and inheritance. Encapsulation describes data hiding by restricting access to instance variables and making accessor methods public. Data abstraction describes a concept or idea that is not associated with any particular instance, allowing abstract class/Interface to express intent without actual implementation. Polymorphism pertains to one name having many forms, both static and dynamic. Static polymorphism uses method overloading, and dynamic polymorphism uses method overriding. Inheritance expresses an is-a or has-a relationship between two objects by reusing existing code based on class inheritance or interface implementation.
Java’s features are inherited from
C and C++ but improved. With Java’s ability to handle run-time
errors, security supported access modifiers, distribution applications,
interactive multi-threading, high performance, and dynamic linking, making Java’s
smooth programming architecture famous for users and developers. Downloading
and installing Java is easy with step-by-step instructions provided by
Oracle’s The Java Tutorials.
- Get link
- X
- Other Apps
Doing What’s Right to Protect Your Network
The
protection of personal data, software, and hardware is the essential goal of
network security. Individuals and organizations must develop and maintain
effective measures to maintain operability and protect information within
computers and networks. I am pursuing a bachelor of science in cyber and data
security technology so that I can help save people and organizations' privacy
and livelihoods.
Until
recent years, network security had not been as vital as it is today. Computers were not networked
before 1980 due to the lack of technology. Back then, serial ports
utilizing RS-232 protocols allowed users to interface with the mainframe
through physically connected terminals to ports. Systems were utterly
vulnerable because they were wide open; security was not considered necessary
due to an emphasis on ease of connectivity and access. Nowadays, a single
network circuit can deliver thousands of connections, and it is imperative to
implement preventative measures that can prevent a security breach.
Network
security is compromised on a foundation of prevention, detection, and
response—the use of security
policies and measures by which an individual or organization develops and
deploys, prevents exploitation of vulnerabilities and deters potential
attackers. Many techniques, devices, and technologies provide rules and configurations
to identify problems to protect a system's network and data. Individuals
and organizations have different determined levels of security that are
individually adequate for them. Information security is considered all of the
following: integrity, confidentiality, authentication, and availability. Simple
policies and procedures that protect information security are data integrity,
backups—disaster recovery, configuration, and media controls.
The
cost-benefit analysis of a compromised network can determine how much one
should invest in security safeguards. The cost to implement network security
measures can be based on the risk and impact of lost data and information.
Three approaches mainly
used in network security are defense-in-depth, obscurity, and perimeter
defense. Perimeter defense uses firewalls to protect against untrusted networks
and cannot protect against an internal attack. A defense-in-depth requires a
combination of all network administrators to harden and monitor all systems.
With this model, an internal network system is better equipped to defend
against a compromised external system like a modem and better protection
against an internal attack. The concept of security by obscurity is in stealth
protection. By hiding a network or system, the ability to be attacked is
decreased. Although, if detected, the network or system is entirely vulnerable.
Some
software and hardware, though design flaws, can allow a system to become
vulnerable and hacked. Once a hacker gains access, a local exploit increases
the privileges of the intruder to a system's network. Another form of
exploitation is a computer worm which is self-contained and replicated. A
computer can become easily infected by a virus with the opening of an email
attachment. Some computers can recover within a few days or weeks but most
never recover.
A combination of multiple layers of defense
can protect a network's security. These layers allow authorized users to access
the network and block malicious threats. The risk of being hacked or attacked
is reduced by implementing
simple and basic procedures: replace outdated computer systems, keep
firewalls on, update all devices to the latest and available firmware, add spam
filters and antivirus/antimalware software, use hacker-proof passwords and
multi-factor authentication, use a virtual private network, limited access
control, wireless security, backup regularly, and have a disaster recovery plan.
All lives will be affected by the evolving and continued growth of information technology. Network security is vital due to the increasing interdependency of the internet and software. One can become overwhelmed and think that network security is not possible, but by implementing basic security measures, a computer's network system can be better protected against potential malicious attacks.
- Get link
- X
- Other Apps
Open-Source Utility Tools
Used to Attack Vulnerable TCP Ports
Free
and open-source utility tools can conduct network discovery, vulnerability
scanning, and password cracking. Send Internet Protocol (IP) packets and
analyze responses that probe innocent individuals' computer networks to scan
ports by pinging using utility tools.
Nmap
Hydra
IT
departments and intermediate computer users combat malicious network attacks
with honeypots, honeynets, and honey; bait systems on a network that confuses,
monitors, and tracks attackers and spammers while identifying new worms
(Kaspersky, 2021). For basic users, the easiest ways to protect a computer from
cyber-attacks is by limiting access to specific information and systems,
regularly updating OS and software, changing administrative passwords on new
devices, installing and activating firewalls, and setting the Wi-Fi router to
use Wi-Fi protected access 2 (WPA-2).
Securing
a network by implementing simple procedures can deter attackers with malicious
intent. The most important way to avoid Nmap or Hydra ping attacks is to
configure the firewalls properly, add filters to the router, install network
monitoring software that alerts unordinary traffic patterns, and regularly scan
a network for open ports. Lastly, when disposing of a computer,
remember to delete all sensitive data before trashing or donating it.
- Get link
- X
- Other Apps
Sale Force-Displacement—Coming Soon
The
need for a good computer and equipment in sales is essential to work
effectively and efficiently. The specific intent for the use of a business
computer will determine which computer system to purchase. A sales team will
need a computer that will allow them to record notes, run demos, build
spreadsheets, and create invoices while staying connected wherever they may be.
Certain detailed computer features are essential: central processing unit
(CPU), graphics card, random-access memory (RAM), optical drives, battery
consumption, security software, connectivity, storage, office suite program,
and a good warranty. A sales company will most
likely need additional equipment: printers, external hard drives, modems, and
possibly smartphones.
Computer
literacy provides individuals with employable skills. Employees who possess a
basic understanding of computers help reduce new employee training costs,
allowing a company to get back on track faster. Computer literate employees
tend to be more efficient if they are proficient with basic office suite
programs. Computer literacy in sales is critical for employees to adapt to new
technological advancements, computer systems, applications, and software.
The
effect of computer evolution on sales can be seen every day—researching and
buying products from home (with same-day package delivery), and machine
learning intelligence that predicts buying patterns and behaviors. Moore's law
is a great observation and projection of future technological growth;
industries are developing products faster, and sales organizations will need to
adapt their company logistics to stay in business. With products launching in
beta stages with quick updates available, product development cycles are shortening
and opening the door for competitors to make product improvements rapidly. New and improved technology is being used to examine market trends by predicting customer needs and behaviors.
Over
the following ten years, computer hardware, operating systems, and networking will create a greater sales force-displacement which can be seen today with
virtual businesses like Amazon and eBay. Artificial intelligence will become more
prevalent in customer service and sales departments. At the same time,
companies will continue building good websites or applications to generate
enormous traffic and sales without needing a sales force.
- Get link
- X
- Other Apps
A computer user can send a ping using Linux user datagram protocol (UDP) or Windows internet control message protocol (ICMP) echo messages to see how long it takes
to reach a remote host, return, and report any loss packets. The
ping is also a way to check if a remote host is active or inactive by sending a
request and waiting for a packet response within a timeout period of 500
milliseconds. The ping process verifies a computer’s connection to the internet
and that it can reach a destination.
I evaluated
three different pings. A ping to google.com resulted in four sent packets, four
received packets and zero packets lost. The approximate round-trip times for
the ping to google.com ping in milli-seconds was a minimum of 25ms, maximum
28ms, and an average of 26ms. A ping to Australia.gov.au resulted in four
packets sent, four packets received, and zero packets lost. The round-trip
times for the ping to Australia.gov.au were a minimum of 15ms, maximum of 20ms,
and an average of 17ms. A ping to Japan.go.jp resulted in four packets sent,
four packets received, and zero packets lost. The round-trip times for the ping
to Japan.go.jp were a minimum of 14ms, maximum of 18ms, and an average of 16ms.
A tracing
route works similarly to a ping but sends three packets of data to test each
hop (Cisco, 2015). A hop refers to a packet passing between routers. However, a
traceroute is used to identify a problematic server causing an error. I
evaluated three different tracing routes. A tracert to google.com with 30 hops
resulted in a minimum 5ms, maximum 42ms, and an average of 23ms. A tracert to
Australia.gov.au with 30 hops resulted in a minimum of 5ms, a maximum of 46ms,
and an average of 17ms. A traceroute to Japan.go.jp with 30 hops resulted in a
minimum of 5ms, a maximum of 27ms, and an average of 17ms.
Both
traceroutes to Japan, and Australia resulted in each having requests timed out
for exceeding the expected 5-second response time. The timed-out requests were
annotated with stars due to possible firewall blocking the ICMP, a router on
the path not sending back the ICMP, or the target IP address not responding.
Although, both traceroutes to Japan and Australia continued on their way and
reached their targets.
Ping of less than 20ms or less are great, between 20-50ms are average, and 50-100ms are considered poor. I was surprised to learn his ping rates to
Japan (16ms), and Australia (17ms) were less than the ping rate to Google
(26ms). The ping rates were excellent and showed the computer was connected to
the internet and reached its target destinations. A ping can be unsuccessful if a target computer is turned off, blocked by a firewall or router. The importance of traceroutes is that their round-trip times should be
consistent. If high latency exists at the beginning of a trace, there could be a problem with one’s local network.
- Get link
- X
- Other Apps
Microsoft Office for Business and Personal Use
Microsoft Office provides application suites designed to assist an individual with productivity and the ability to complete a wide variety of tasks—applications can be used together to maximize efficiency. When describing the daily functions of one day, this author used Microsoft Excel, Word, and PowerPoint to create and edit text documents, images, presentations, and spreadsheets with data.
Microsoft Word processor is considered to be the most commonly used program of the Microsoft Office Suite. Microsoft Word has many design templates and page layout options for creating formatted texts. This author created a text document with Microsoft Word. The paper consisted of "One Day In My Life." Editing and formatting are easy to learn, making the document interactive using different features and tools: bullet points, fonts, bold, highlights, underlines, and spell-check. Additionally, an individual can also use Microsoft Word to create reports, write a novel, resumes, grocery lists, etc.

Excel is a spreadsheet program used for documenting data analysis. By formatting cells and formulas, an individual can easily modify Excel's columns and rows, functions, sorting and filing, and charts. Excel helped me to create a spreadsheet to better depict “One Day in My Life”. I used the math functions to create a formula the spreadsheet could calculate the sum and percentages of tasks per hour throughout one day. I also used Excel to add a pie chart to this author's report that displayed ratios and a formatted legend. Individuals can also use Excel to create sales reports, timecards, billing statements, balancing budgets, etc.

A PowerPoint computer
application allows users to create a slide show that provides visuals for group
presentations using slides, recordings, transitions, and narrations. This author created a PowerPoint presentation depicting "One Day In My Life". PowerPoint was easy to learn, and this author used
different features and tools: fonts, bold, bullet points, color, images, sound,
animated transitions, and animations of elements. Individuals in various capacities can also use
PowerPoint for presentations: business, clergy, teachers, students,
etc.
PowerPoint would be ideal for a large group presentation because of the more personal interaction and ability to gauge an audience. Excel is perfect for providing the specific data and information along with a chart for display. With good communication skills and an ability to engage and collaborate with an audience, I would prefer to use a PowerPoint presentation.
- Get link
- X
- Other Apps
A Review of the Pool Calculator App
ThePool Calculator provides a swimming pool owner with necessary tools along with pool maintenance information needed to keep their water clear and balanced. The popularity of the Pool Calculator is the ease in which it can estimate how much of a chemical needs to be added to a pool. The Pool Calculator was designed with easy to learn basic computing commands that help to adjust pool chemicals efficiently. The functions of the Pool Calculator are easy to remember, and it works flawlessly—unless a user inputs the wrong information or incorrectly measures their pool chemicals.
The Pool Calculator design has a simple user interface (UI) and a friendly user experience (UX); both Android and iOS can use the app. At first glance, the app shows the multiple categories which it can calculate: pool volume, chlorine, salt, the potential of hydrogen (PH), alkalinity, stabilizer, borate, heat time, turnover rate, filter size, flow rate, dynamic head, calcium hardness, and saturation index. The simplicity and easy readability of the Pool Calculator is the key to the app's popularity and easy functionality. For example, the app's wireframes help users understand, navigate, and use standard buttons and icons. The tabbed menu is located in the upper right-hand corner. Each category is tabbed, delivering a streamlined focus and meeting the users' needs with its design and functionality.
After I take a water sample of my swimming pool, I use a standard test kit for testing my pool water chemistry. By testing my pool water, I can input the current chlorine, PH, or alkalinity readings into the app and be provided with the number of needed chemicals to achieve the desired range with the press of a tab. The Pool Calculator helps me maintain proper chlorine, PH, and alkalinity, the main chemicals I monitor year-round in my swimming pool. I personalize the app by pre-setting the 17,500 gallons my pool holds. The ability to store and pre-set the gallons my pool has helps tailor the content when I visit the app. The Pool Calculator was developed to provide fast load times. Filtering and sorting make the process of browsing appear seamless. As a user, I appreciate the Pool Calculators' speed and simplicity. The Pool Calculator has helped give me the confidence to maintain my pool without hiring a local pool company. The average charge for pool maintenance in my area is $125 per month. The Pool Calculator is a free app that can be downloaded to help any pool owner who wants to maintain their pool.
A few recommendations for improving the Pool Calculator are the addition of an
appropriate chemical level guideline, calculation based on outdoor
temperatures, and the tracking of previous pool test logs. By providing a
chemical levels guideline, app users will not have to search the internet for
the desired range of chemicals needed. Adding a calculator that considers the
outdoor temperatures can help individuals who live in climates that vary
year-round. Pool owners can estimate the
cost of chemicals throughout the year if the Pool Calculator could record or
log all previous pool tests. The feature could help the Pool Calculator users
by providing an average amount of chemical usage. The user can then know how
many chemicals to purchase when going to the pool supply store.
- Get link
- X
- Other Apps
Scratch is a website dedicated to inspiring individuals who are
new to programming language. A person can create an interactive animation
within minutes by using blocks versus syntax. The
tutorials within the scratch website provide easy step-by-step
instructions for those learning to Scratch or not to Scratch.
The primary
challenge I encountered was my lack of knowledge and prior programming
experience. However, after watching Scratch tutorials I was inspired and
excited to Scratch. I
learned how to create an interactive animation through tutorials
provided on the Scratch website. The tutorials helped me understand the
structure and logic to plan a layout design/backdrop using sprite actions in a
simple and visual interface. The functionality of the stage layout
reminded me of the 0’s and 1’s of machine language, including the Central
Processing Unit (CPU) instructions: input, add, output, stop, subtract,
multiply, divide, jump, etc. Practicing and learning to run basic Python
programs in my Fundamentals of
Information Technology & Literacy college class, helped me better understand the use of the
Scratch blocks.
Scratch is
different from Python because of its graphical logic blocks programming
approach, which allows for animation, sounds, and graphics without detailed
syntax; users do not have to enter source code manually. Python language can
become complicated for new users due to the source code and language
punctuation needed to create text output.
The Scratch
program language was easier to work worth than Python due to importing graphics
and sounds. Scratch allowed me to quickly learn control structures, variables,
and operators using building blocks. The progression of higher-level
programming during Scratch is an issue when combining and stopping multiple
simultaneous sounds.
Scratch would be
most popular with beginners new to programming; Python would be preferred by
experienced software developers due to the use of more sophisticated language
capabilities of function calls and editing through textual code. For
developers, the use of Python enables the use of many tools. For example, integrated
development environments (IDE) have a central interface with multiple
tools: code editor, compiler, debugger, and build automation tools.
By choosing to Scratch, Scratch’s simplicity and programming environment provided me with an exciting and invaluable programming learning experience that will guide me throughout my information technology career.
- Get link
- X
- Other Apps